On Wednesday, November 27, 2019 I experienced a scary spear-phishing cyber attack. Emotionally I was humiliated. I felt extremely vulnerable and violated. I felt helpless and deeply incapacitated.
What is a spear-phishing attack?
According to www.kaspersky.com, spear phishing is an email or electronic communication scam targeted towards a specific individual, organization or business. The purpose of such an attack is to steal data for malicious purposes or to install malware on a targeted user’s computer.
The purpose of this post is to share my experience with this type of cyber attack or cyber crime.
At the SEACEN Centre, my responsibilities include serving as course director for our Information Communication and Technology (ICT) Risk courses. These courses typically focus on cyber threats and cyber security as well as the concepts and mechanics of risk assessment by bank supervisors. As the course director, I also serve as a resource person for at least one session during our ICT Risk courses. For example, at the Bank of Japan-SEACEN ICT Risks, including Cybersecurity Course hosted by the State Bank of Vietnam in Hanoi in August 2019, I presented a session on emerging technologies and risks. The main focus of the session was deep fake videos and other sophisticated trends in cyber attacks.
Based on my knowledge and experience, please allow me to highlight two things to keep in mind. They are:
(i) my job provides me with lots of opportunities to build awareness and education relating to cyber threats and how to prevent falling victim to an attack; and
(ii) based on my work I am constantly interacting with cybersecurity experts including the wonderful staff at CyberSecurityMalaysia, The Financial Services Information Sharing and Analysis Center (FS-ISAC) and Law enforcement Agencies.
The message here is simple, I should know this:
UNDER ABSOLUTELY NO CIRCUMSTANCES, NEVER, EVER OPEN AN EMAIL WITH AN ATTACHMENT OR HYPERLINK FROM AN UNKNOWN SENDER OR UNKNOWN EMAIL ADDRESS.
THIS IS A GOLDEN RULE in cybersecurity and I violated this rule.
Since my experience in November, I have asked myself some fundamental questions about cyber-threats and cybersecurity. They are:
Given the increasing use of technologies in the delivery of financial services and products, especially to the unbanked and underserved, how do we safeguard the most vulnerable and unsophisticated people in our societies?
Let us call a spade a spade. I should not have fallen victim to this type of spear-phishing attack given my knowledge and information. I have been provided with the “necessary” training and awareness required to protect myself and The SEACEN Centre and its members.
Why did I fall so easily victim to this spear-phishing attack? I am of the firm belief that people are the weakest link when it comes to cyber threats and cyber security.
A comprehensive cybersecurity strategy incorporates three “P’s”. They are security technology products, policies and processes, and highly trained people. Businesses can dramatically increase their odds of successfully managing all three factors if they help ensure that security is embedded into every layer of the organization instead of being bolted on ad hoc on an as-needed basis.
Other related question, are:
What additional training and awareness would be necessary for me? What cybersecurity education and awareness would be required by those individuals who are being given access to banking and financial services as part of policies aimed at wider financial inclusion?
How does a spear-phishing attack works?
Aside from brute-force attacks by shadowy hackers, the next biggest and often most insidious form of cybercrime comes via phishing. It is imperative to understand the importance of (i) frequently running patches and updates, (ii) using strong passwords, and (iii) what is phishing and how to protect against phishing. This can help lead to a healthy cybersecurity environment that can protect business data and prevent a ransomware attack.
According to www.kaspersky.com with spear-phishing, an email arrives, apparently from a trustworthy source, but instead it leads the unknowing recipient to a bogus website full of malware. These emails often use clever tactics to get victims’ attention. Below is a snapshot of the email I received.
A copy of the email I received is shown below. I will now share three pieces of details to help provide some context and background for you.
1. The Subject Line: Wire Payment
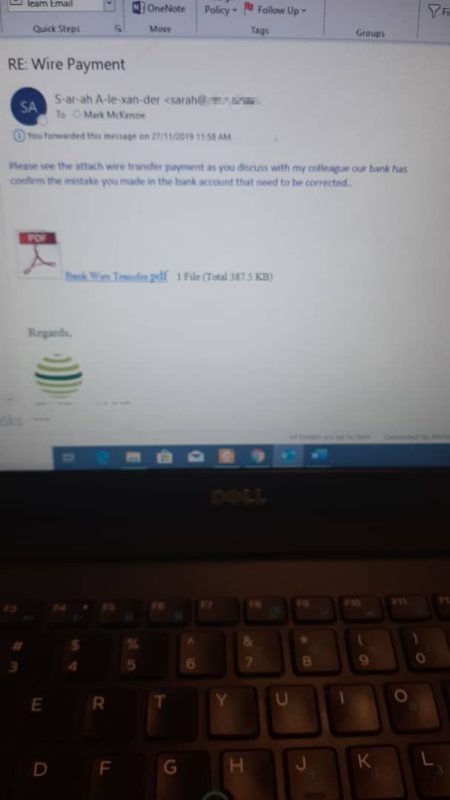
The subject line wire payment is relevant, and this was truly one of the scary parts about my attack for a number of reasons. Psychologically, how did the hacker or hackers know to use “wire payment” in the subject line?
In my attempt to answer this question, please allow me to share some additional background information. Twice per month I use my Malaysian bank’s online banking services to transfer money back home to Canada. Please note that my spear-phishing attack occurred just around the time of the month that I typically execute my online cross-border fund transfer.
Another important detail about my typical online transaction is the fact that I structure my transaction into two separate transactions, roughly a week apart of each other. I do this mainly because of my bank’s limit on the transaction size per transaction. For example, let’s say my bank only allows daily transfer of USD 2,500 using its online service, and I want to remit the equivalent of USD 5,000 abroad. Using this example, I can use my bank’s online services to execute two (2) transactions of equal sizes on separate days.
The alternative to structuring the transaction would be to visit a branch of my Malaysian bank once per month and do a single transaction. But who visits banks these days?
Another interesting fact is that on Tuesday, November 26, 2019 (the attack was on Wednesday), I did physically visit my bank’s branch to execute a wire transfer. I visited the bank because I wanted to transfer a larger amount than the aggregate of the two transactions that I normally do for online transfers. Furthermore, the amount would have met the banks’ mandatory AML/CFT reporting threshold either as a single transaction or aggregated, if structured.
Using the example above, let us say that in November rather than remitting USD 5,000, the amount was USD 10,000. Under the FATF’s Standards, USD 10,000 is an important reporting limit for monitoring the proceeds of crime and money laundering. If I wanted to successfully remit USD 10,000 overseas using my bank’s online services, I would need to do four (4) separate transactions on different days. Using this approach to execute the transaction would obviously increase both the time and cost of my transaction.
So, how did the hacker or hackers know to use “wire payment” in the subject line? Did the hacker or hackers know that I visited my bank on the day before their spear-phishing attack?
There are two possible answers to this questions, and they are:
- It could very well be that they are already tracking me online and they already know the time of the month I do my online wire transfers; and
- Alternatively, it could be they are monitoring all outbound wire transfers, and given details that they already have on me they were able to escalate their attack in November.
Both scenarios are are consistent with the following:
- It is not a matter if you will be attacked, it is matter of when you will be attacked. It is also about knowing whether you have been attacked.
- Systems and devices can be infected with malware and viruses that sit in the background and wait for the opportune time to launch like the execution of the 2016 Central Bank of Bangladesh’s USD 101 million Heist.
- They can also sit in the background and stealthily collect small bits of information before stealing data. For example, the 2018 cyberattack on the Singapore government’s health database that stole the personal information of about 1.5 million people, including Prime Minister Lee Hsien Loong.
2. Email Address
Frankly, I don’t know the sender and I don’t know the email address. Let me reiterate, I violated the golden rule when clicking on the hyperlink.
Allow me to point out that my Malaysian bank occasionally send me emails on certain transactions or account activities. Below I share a snapshot of a legitimate email from my Malaysian bank.

If you take a closer look at the name of the sender in the spear-phishing email, you will see that it appeared with a lot of “-“ in the spelling. In addition, a single letter marked the main difference between my Malaysian bank’s email address and the fake bank’s email address. For example, realbank@real.com vs S-ar-ah A-le-xan-der@rel.com.
The use of “-“ in the spelling of the sender’s name should have made it very obvious this was a fake email but I missed it. Equally important, I also overlooked the crucial detail of the missing letter between my bank’s email address and the fake bank’s email address.
How did I miss these crucial pieces of details? Psychologically, a spear-phishing email is designed to hook the intended target. Please remember that people are perhaps the weakest link in cybersecurity.
Please look closely at @real.com vs @rel.com. The difference is very easy to tell when it is presented this way.
How easily can you spot the differences in the following?
a. S-ar-ah A-le-xan-der@real.com vs S-ar-ah A-le-xan-der@rel.com?
b. realbank@real.com vs S-ar-ah A-le-xan-der@rel.com?
c. sarah@real.com vs sarah@rel.com
3. The Text In The Body of the Email
The text in the body of the email is written in blue and read:
“Please see attached transfer payment as you discussed with my colleague our bank has confirmed the mistake you made in the bank account that need to be corrected.”
I will leave you to be the judge. Acting on emotions and impulse I clicked “Bank Wire Transfer.pdf”.
Hindsight is twenty-twenty. I never spoke with anyone at any bank about any mistake made on any bank account or wire transfer. Knowing this, I should never have clicked on the link.
Phishing and spear-phishing attacks are designed to exploit the intended target’s emotions and vulnerabilities. I can give you multiple reasons, why psychologically and emotionally I desperately wanted to ensure that my wire transfer was not delayed, but you can be the judge. However, please ask yourself, why was the amount of my wire transfer in November larger than the aggregate of the two online transfers I typically do each month?
Frankly, I doubt the hacker or hackers knew the answer to this question, but if they do, I am afraid that would be an even much scarier thought!
According to www.kaspersky.com, many times government-sponsored hackers and hacktivists are behind these attacks. Cyber criminals do the same with the intention to resell confidential data to governments and private companies. These cyber criminals employ individually designed approaches and social engineering techniques to effectively personalize messages and websites. As a result, even high-ranking targets within organizations, like top executives, can find themselves opening emails they thought were safe. That slip-up enables cyber criminals to steal the data they need in order to attack their networks.
According to SEACEN’s IT personnel, because of my social media presence on Facebook, Instagram, Twitter and Linkedin, and my visibility in the community including speaking at conferences, I am a high value target for spear-phishing and social engineering tactics.
Other cybersecurity experts have told me that my devices are perhaps already compromised. This might explain why I frequently receive phishing emails.
Where did clicking on the link in spear-phishing email take me?
When I clicked on the link in the spear-phishing email, it took me directly to a page requiring me to sign in to my Onedrive on the cloud. It was only at that point that I realized I was spear-phished. Consequently, I did not sign into my account. It was also at that moment that I informed my IT colleagues. I also visited my Malaysian bank’s website to see if I could report the incident or share my experience.
Today, I am deeply worried that there is a malware or ramsomware lurking in the dark using artificial intelligence to clandestinely track and monitor all my activities online. It is stealthily lurking and patiently waiting for the right moment to execute its nefarious intentions.
How to Protect Yourself?
According to www.kaspersky.com, traditional security often doesn’t stop these attacks because they are so cleverly customized. As a result, they’re becoming more difficult to detect. One employee mistake can have serious consequences for businesses, governments and even nonprofit organizations. With stolen data, fraudsters can reveal commercially sensitive information, manipulate stock prices or commit various acts of espionage. In addition, spear phishing attacks can deploy malware to hijack computers, organizing them into enormous networks called botnets that can be used for denial of service attacks.
To fight spear phishing scams, employees need to be aware of the threats, such as the possibility of bogus emails landing in their inbox. Besides education, technology that focuses on email security is necessary.
Mark is a Senior Financial Sector Specialist in the Financial Stability, Supervision and Payments pillar at the SEACEN Centre.

